Cloudflare and Caddy Mutual TLS
Recently I deployed a TeslaMate on an Azure virtual machine. Since TeslaMate doesn’t support any authentication, and to apply defense by depth, I’m trying to make the whole network traffic from browser to Azure VM is encrypted.
Cloudflare to Azure
Cloudflare authenticate my VM
On Cloudflare dashboard, it can set SSL/TLS encryption mode:
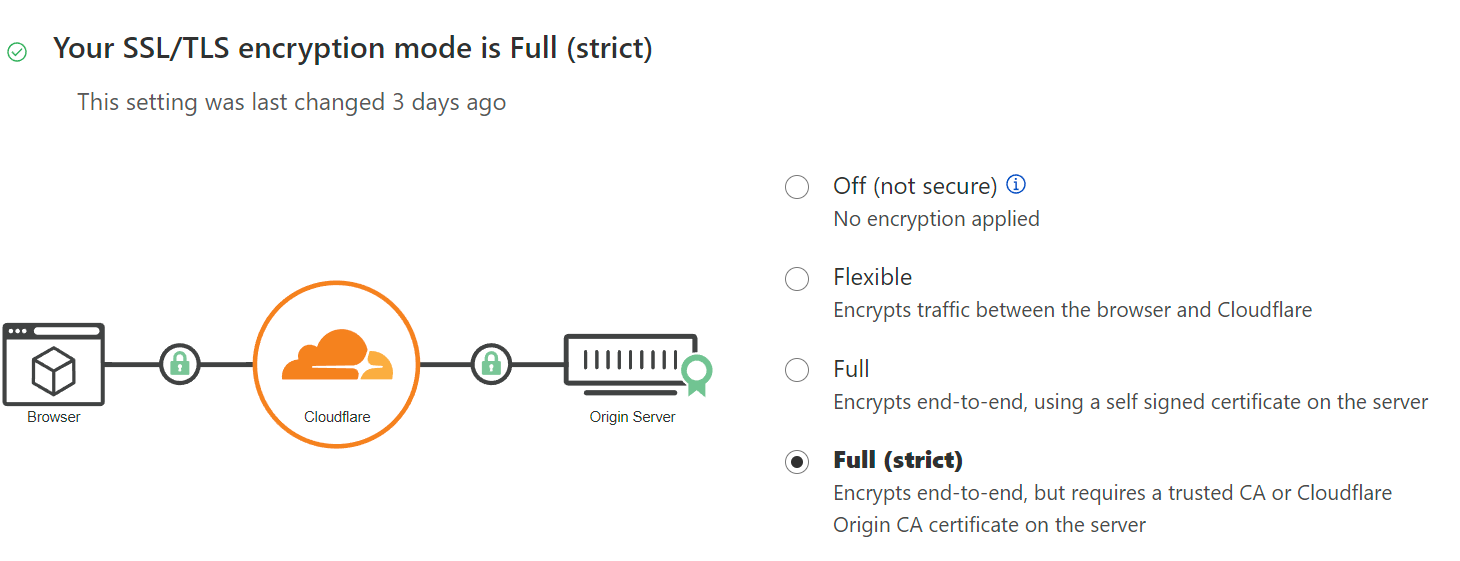
Full mode requires a trusted CA certificate or a certificate generated by Cloudflare. I choose the later one as it has 20 years validation date, so do not need to use ACME every 3 months (like LetsEncrypt).
> It's possible to automatically request and deploy certificate, some webservers like Caddy has built-in mechanism to refresh server certificate.
On Cloudflare dashboard, create a new origin server certificate here
Then deploy certificate and key on the server (Never share certificate private key on the internet)
In Caddyfile, enable TLS with certificate and key:
tls /cert/cloudflare_origin.pem /cert/cloudflare_origin.key
VM authenticate requests from Cloudflare
In the virtual machine, I would like all requests are sent from Cloudflare. Their are few ways to do so, like restrict IP range, sign the network request etc… But for Cloudflare free version, the recommended way is “Authenticated Original Pulls“. “Origin Pulls” are the requests from Cloudflare to user’s origin server (In my case, the Virtual Machine on Azure). Cloudflare will send TLS client certificate to origin server, on the VM we can check the cert and block other requests directly sent from user. On Cloudflare dashboard, enable “Authenticated Origin Pulls”:
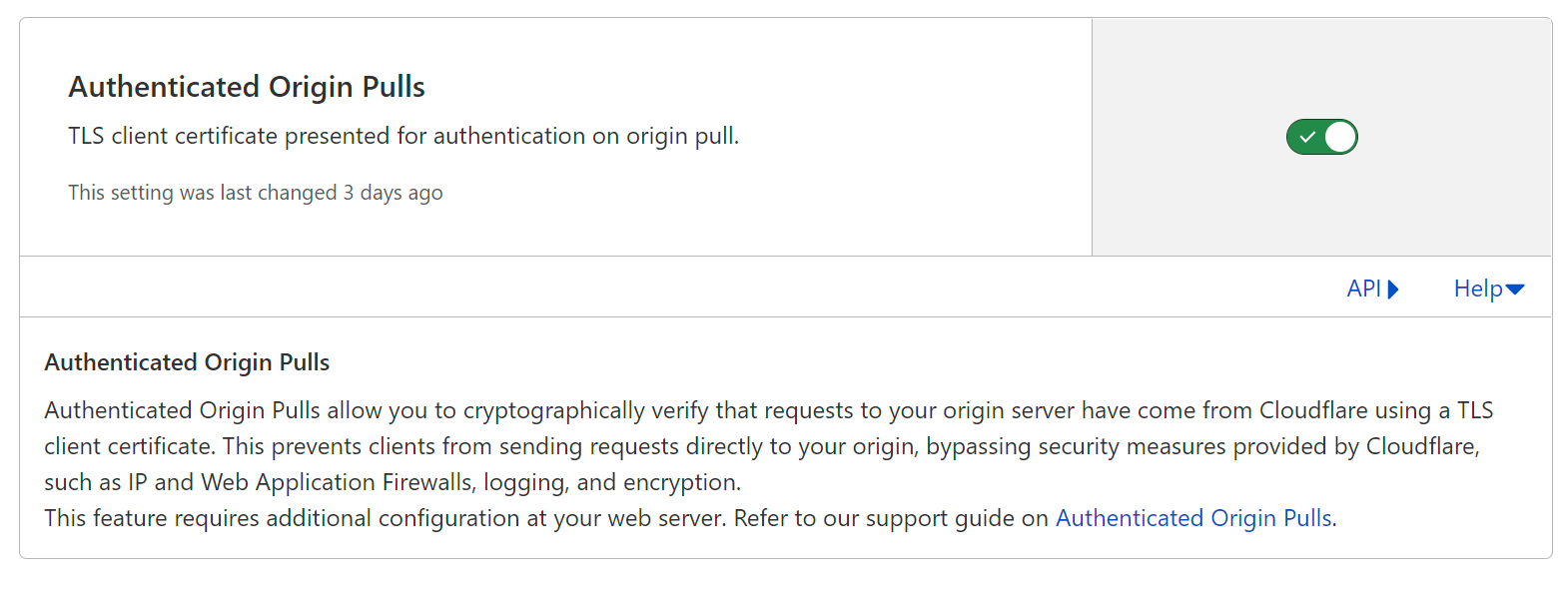
On VM, we need to download Cloudflare CA certificate first, then enable TLS client auth in Caddy:
1 | client_auth { |
Browser to Cloudflare
To archive only authenticated user (myself explicitly) can visit that site, we can add authentication on the VM or Cloudflare side. Such as HTTP basic auth, or signin (first party or third party). Cloudflare supports TLS client certificate on the Edge server, which gives Cloudflare ability to cryptographically verify it’s myself. This requires user to install certificate on device first:

Then we need to set Cloudflare firewall to block requests without Client certificate, just follow guide on Cloudflare dashboard.